Why Choose Cyber Rely for Web Application Penetration Testing?
- Deliver highly secure applications while reducing compliance costs.
- Local Security Policy Bypassing.
- Find business and logic flaws that are missed by other forms of automated testing.
- Secure applications from leaking sensitive customer data
- Remove Complexity with Vulnerability Management and Patching.
- Reduce Compliance Costs and Continuous Security Monitoring
- Reduce Time to Identify and Fix Security Vulnerabilities.
- Secure applications from leaking sensitive customer data
- Remove Complexity with Vulnerability Management and Patching.
- Increase the speed and quality with which developers deliver secure code.
- Utilize dashboards to monitor the security posture and history of applications.
- Utilize cybersecurity as a competitive advantage.
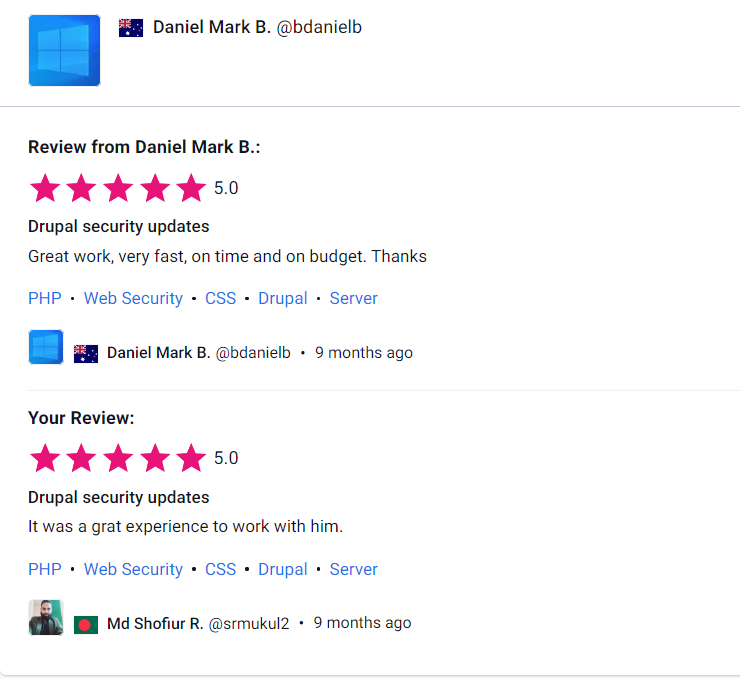
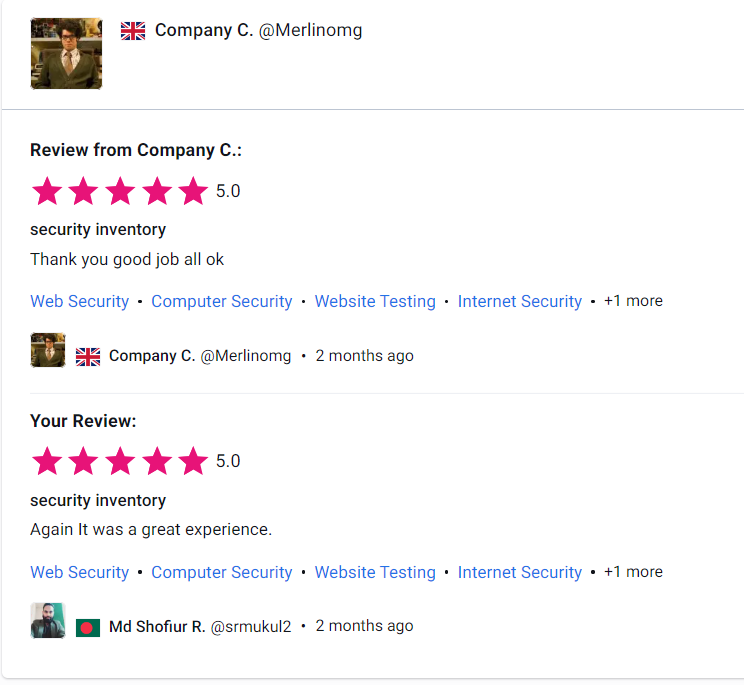
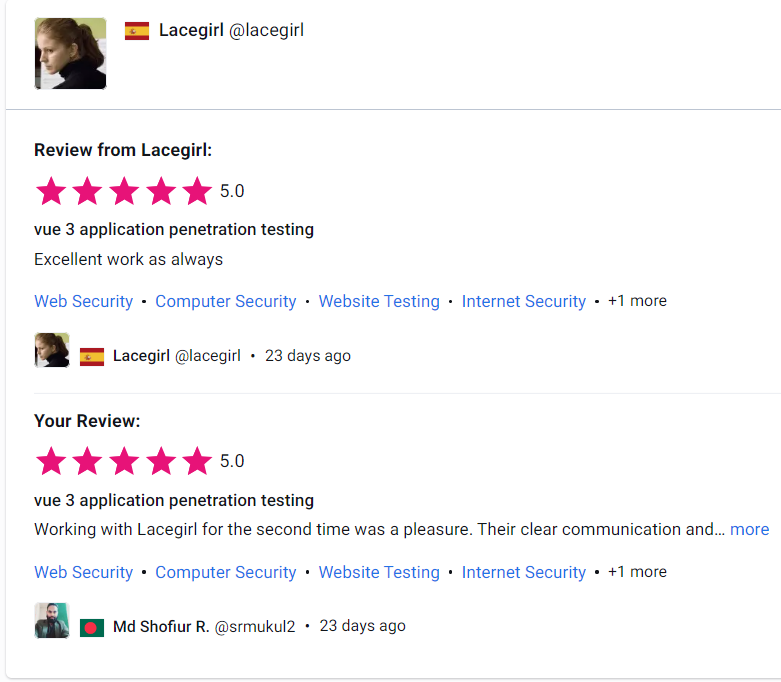
Customer Reviews
Web Application Penetration Testing as a Service Business Benefits?
We have collaborated with a variety of industries, including Airlines, Supply chains, Fintech, Health-tech, e-commerce, etc. We believe that a pentest will have the greatest impact on a company when the pentesting team has a thorough understanding of the web application’s business logic. Therefore, we dedicate a specialized team to comprehending the business logic of the issue at hand.
- Simulate Attacks to Evaluate Your Security Posture
- Improve the speed and quality of developers’ secure code builds.
- Reduce testing costs without compromising security.
- Deliver highly secure applications while reducing compliance costs.
- Prevent Security Testing from Delaying Application Release, Eliminate Complexity through Vulnerability Management and Upgrades.
- Reduce the time and effort required to identify and fix security flaws.
- Secure coding training for developers reduces the cost of security testing.
- Monitoring dashboards for your web application’s security posture.
Our testing methodology goes beyond surface-level assessments to uncover vulnerabilities lurking within both the application and its back-end services. We meticulously examine every component to ensure comprehensive coverage. Leveraging advanced techniques such as reverse engineering, binary, and file-level analysis, we delve deep into the system’s architecture to unearth even the most elusive vulnerabilities. This approach surpasses standard penetration testing, providing thorough and effective security assessments.
These security testing activities may include but are not limited to:
- Broken Access Control
- Insecure Direct Object Reference (IDOR)
- Structured Query Language Injection
- Response Manipulation
- Software and Data Integrity Failures
- Server-Side Request Forgery
- Local and Remote File Inclusions
- Response Manipulation.
- Insecure file parsing.
- Service misconfigurations.
- Information Gathering
- Information Analysis
- Vulnerability Detection
- Penetration Testing
- Privilege escalation
- Result Analysis
- Reporting
- Security Briefing Workshop
- Mitigation Support
- Complementary Retesting
- Summary Report