Top 5 Best Practices to Prevent CORS Misconfigurations in TypeScript-Based ERP Systems
Introduction
Cross-Origin Resource Sharing (CORS) is a critical security feature that controls how web applications interact with resources from different origins. In TypeScript-based Enterprise Resource Planning (ERP) systems, improper CORS configurations can expose sensitive data and functionalities to unauthorized domains, leading to significant security vulnerabilities.

This article delves into the best practices to prevent CORS Misconfigurations in TypeScript-Based ERP Systems, providing practical coding examples to guide developers toward secure implementations.
Understanding CORS in TypeScript-Based ERP Systems
CORS is a security mechanism implemented in web browsers to restrict web pages from making requests to a different domain than the one that served the web page. While this policy enhances security, it can pose challenges in ERP systems that often require interactions across multiple domains.
Misconfigurations in CORS can lead to:
✅ Unauthorized access to sensitive resources
✅ Data leaks and security breaches
✅ Exploitation of application functionalities by malicious actors
Common CORS Misconfigurations
Here are some common CORS misconfigurations that can make your ERP system vulnerable:
- Overly Permissive Origins – Allowing all origins (
*) can expose the application to malicious domains. - Improper Use of Credentials – Incorrect handling of credentials can lead to unauthorized data access.
- Lack of Proper HTTP Methods and Headers Validation – Not validating HTTP methods and headers can open avenues for exploitation.
Top 5 Best Practices to Prevent CORS Misconfigurations
1. Restrict Specific Origins
Instead of allowing all origins, specify the trusted domains that can access your resources.
Here’s how to configure CORS in a TypeScript-based ERP system using Express:
import express from 'express';
import cors from 'cors';
const app = express();
const allowedOrigins = ['https://trusted-domain.com', 'https://another-trusted-domain.com'];
const corsOptions = {
origin: (origin, callback) => {
if (allowedOrigins.includes(origin)) {
callback(null, true);
} else {
callback(new Error('Not allowed by CORS'));
}
},
};
app.use(cors(corsOptions));
app.get('/api/data', (req, res) => {
res.json({ message: 'This is secured data.' });
});
app.listen(3000, () => {
console.log('Server running on port 3000');
});👉 In this configuration, only the specified domains are permitted to access the /api/data endpoint.
2. Handle Credentials Securely
If your application needs to handle credentials such as cookies or HTTP authentication, ensure that the Access-Control-Allow-Credentials header is set appropriately, and avoid using the wildcard (*) for the Access-Control-Allow-Origin header.
Secure CORS Configuration for Credentials Handling
const corsOptions = {
origin: 'https://trusted-domain.com',
credentials: true,
};
app.use(cors(corsOptions));💡 This setup allows credentials to be included in requests from https://trusted-domain.com.
3. Validate HTTP Methods and Headers
Explicitly specifying allowed HTTP methods and headers prevents unauthorized actions.
CORS Configuration for HTTP Methods and Headers
const corsOptions = {
origin: 'https://trusted-domain.com',
methods: ['GET', 'POST', 'PUT', 'DELETE'],
allowedHeaders: ['Content-Type', 'Authorization'],
};
app.use(cors(corsOptions));🔹 This configuration restricts the allowed HTTP methods and headers to a predefined set, enhancing security.
4. Implement Preflight Request Handling
Browsers send a preflight request (OPTIONS method) to determine if the actual request is safe to send. Ensure your server correctly handles these preflight requests.
Enable CORS Preflight Handling
app.options('/api/data', cors(corsOptions));✅ This line enables CORS preflight handling for the /api/data endpoint.
5. Regularly Review and Test CORS Configurations
Regularly auditing your CORS settings ensures they align with your security requirements. Utilize security testing tools to check for potential vulnerabilities.
You can use our free website security scanner to assess your CORS settings and overall security posture.
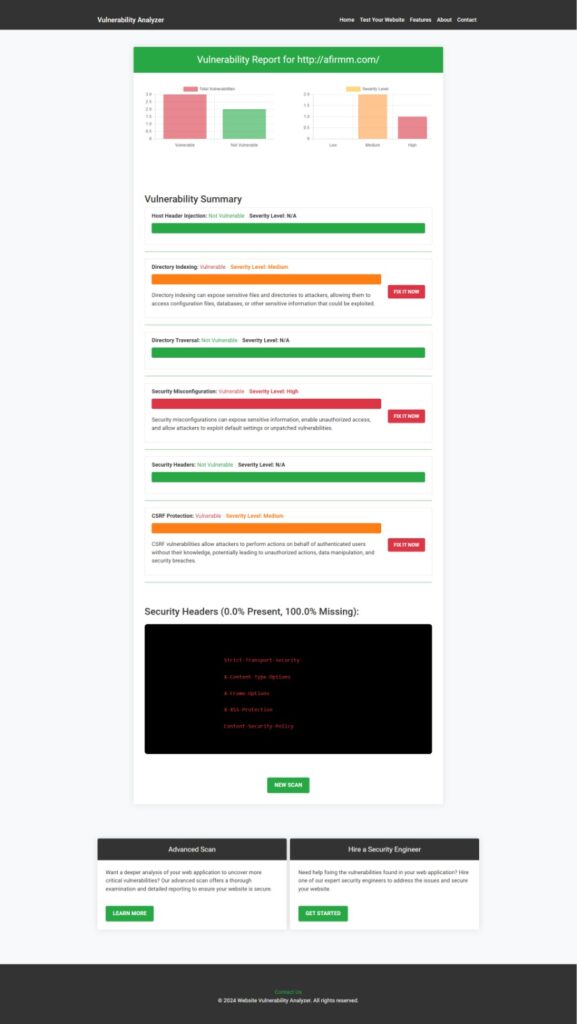
📌 Example Screenshot of Free Website Vulnerability Scanner:

After scanning, you’ll receive a detailed vulnerability assessment report to help you identify and fix security issues.
📌 Example Screenshot of Vulnerability Assessment Report to check Website Vulnerability:
Conclusion
Preventing CORS Misconfigurations in TypeScript-Based ERP Systems is crucial for maintaining the security and integrity of your applications. By implementing these best practices and regularly reviewing your configurations, you can safeguard your system against potential threats.
🔗 For more insights on securing TypeScript applications, check out our article on Fixing Weak SSL/TLS Configurations in TypeScript.
🔗 Additionally, our previous posts on:
✅ Transport Layer Protection in TypeScript-ERP
✅ Fixing Weak Password Policies in TypeScript
✅ React JS Apps Vulnerability Assessments
✅ Visit our Blog for More
For advanced security solutions, explore our services at Pentest Testing.
By following these guidelines and leveraging available resources like our free tool for a quick website security test, you can effectively prevent CORS misconfigurations and enhance the security of your TypeScript-based ERP system. 🚀
Pingback: Transport Layer Protection in TypeScript-ERP: Best 5 Fixes