SQL Injection (SQLi) Vulnerabilities in OpenCart: Detection & Prevention
Introduction to SQL Injection (SQLi) in OpenCart
SQL Injection (SQLi) is one of the most critical security vulnerabilities affecting e-commerce platforms like OpenCart. This threat arises when attackers inject malicious SQL code into your database queries, potentially allowing them unauthorized access to customer data, admin credentials, and other sensitive information.
In this article, we will explore the basics of SQL injection in OpenCart, walk through an example of how vulnerabilities might look in code, and discuss effective prevention techniques to secure your platform.

Understanding SQL Injection (SQLi) in OpenCart
OpenCart relies heavily on SQL databases for handling product listings, customer accounts, and transaction data. Unfortunately, this makes it susceptible to SQL injection attacks if input fields and URLs are not properly sanitized. SQL injection occurs when an attacker is able to add or “inject” SQL statements into a query, manipulating the database’s actions.
Let’s take a look at a common example of vulnerable code in OpenCart:
php// Vulnerable code example
$productId = $_GET['id'];
$query = "SELECT * FROM products WHERE id = '$productId'";
// Executing the query
$result = $db->query($query);
In this example, if an attacker inputs a crafted SQL statement into the id parameter (e.g., 1 OR 1=1), they could access all product data without any authentication.
Preventing SQL Injection in OpenCart
To prevent SQL injections in OpenCart, you should always use prepared statements or parameterized queries. Here’s how the example above can be modified to prevent SQLi attacks:
php// Safe code example using prepared statements
$productId = $_GET['id'];
$query = "SELECT * FROM products WHERE id = ?";
$stmt = $db->prepare($query);
$stmt->bind_param("i", $productId);
$stmt->execute();
By using bind_param, we ensure that the input is treated strictly as a value, not executable code, thereby preventing any malicious SQL injection attempts.
Protecting Your OpenCart Store with Free Tools
To make sure your site is secure from SQL injection vulnerabilities, it’s essential to conduct regular vulnerability assessments. At Pentest Testing’s Free Tools, you’ll find comprehensive tools designed to assess and detect SQLi risks efficiently.

These tools can simulate SQLi attacks on your OpenCart website, giving you insights into how secure your platform really is.
Analyzing the Vulnerability Report
After running the SQLi test, you will receive a detailed vulnerability assessment report. Here’s an example screenshot of a report generated by our free tool, highlighting potential SQL injection vulnerabilities and remediation steps.
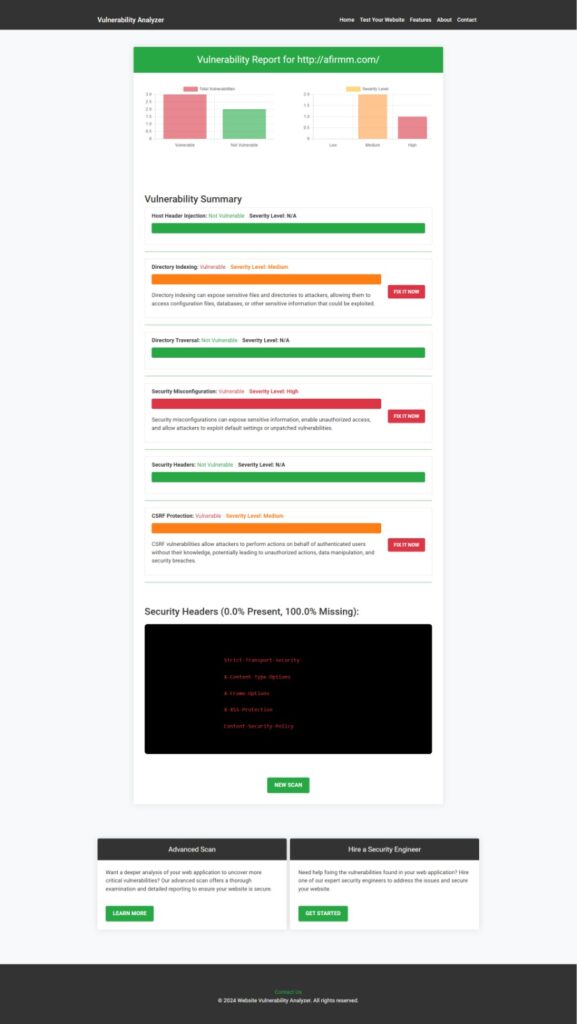
The report outlines specific SQLi risks and suggests mitigative measures, such as parameterizing queries, enabling database security layers, and restricting user permissions.
Further Resources and Professional Pentesting Services
For those who manage multiple e-commerce sites or need advanced assistance, we recommend consulting our other websites PentestTesting.com and CyberRely.com for professional-grade cybersecurity solutions, including vulnerability assessments and penetration testing. We specialize in securing OpenCart and other e-commerce platforms against SQLi and other security threats.
Conclusion
Securing your OpenCart platform against SQL injection is essential for safeguarding customer data and ensuring site stability. With best practices in coding and regular vulnerability testing, your store can effectively prevent SQLi attacks.