5 Crucial Fixes for Insecure Direct Object References IDOR in TypeScript-Based ERP
Understanding IDOR in TypeScript-Based ERP Systems
Insecure Direct Object References (IDOR) is one of the most prevalent vulnerabilities in web applications and ERP systems. When security checks are bypassed, malicious users can directly access unauthorized data or resources. In a TypeScript-based ERP system, the risks of IDOR increase due to the interconnected nature of modules handling sensitive business information.
In this post, we’ll delve into practical solutions to mitigate IDOR vulnerabilities using TypeScript, share a coding example, and discuss tools you can use to identify these risks.

What is IDOR and Why Does It Matter?
IDOR occurs when an application provides direct access to objects like files, records, or database entries based on user-supplied input without validating the user’s authorization. This vulnerability can lead to unauthorized access, data leaks, or even full system compromise.
For example, an ERP system might have an endpoint to retrieve order details using:
GET /api/orders/12345 If the application doesn’t validate the user’s permissions, any user can potentially access or modify another user’s data by changing the order ID.
How IDOR Manifests in TypeScript-Based ERP Systems
Let’s consider a TypeScript-based ERP system handling customer invoices:
app.get('/invoice/:id', async (req, res) => {
const invoiceId = req.params.id;
const invoice = await database.getInvoiceById(invoiceId);
res.json(invoice);
});In the above code:
- The
invoiceIdis extracted from the URL. - The corresponding invoice is fetched and sent to the user without verifying their permissions.
This logic creates an IDOR vulnerability because any logged-in user can access any invoice by simply changing the id.
A Secure TypeScript Implementation
Here’s how you can fix this issue using role-based access control (RBAC):
app.get('/invoice/:id', async (req, res) => {
const invoiceId = req.params.id;
const userId = req.user.id; // Extracted from authentication middleware
const invoice = await database.getInvoiceById(invoiceId);
if (invoice.userId !== userId) {
return res.status(403).json({ error: 'Access denied' });
}
res.json(invoice);
});This implementation ensures the userId in the invoice matches the currently logged-in user.
5 Steps to Prevent IDOR in TypeScript ERP Systems
- Implement Middleware for Authorization
Use middleware to validate every API request for appropriate access rights. - Avoid Direct Object References
Replace direct IDs with hashed or obfuscated values like UUIDs.
Example:const obfuscatedId = generateUUID(invoice.id); - Use Parameterized Queries
Prevent tampering by validating all user inputs. - Educate Development Teams
Ensure teams understand common security risks like IDOR and apply secure coding practices. - Conduct Regular Vulnerability Assessments
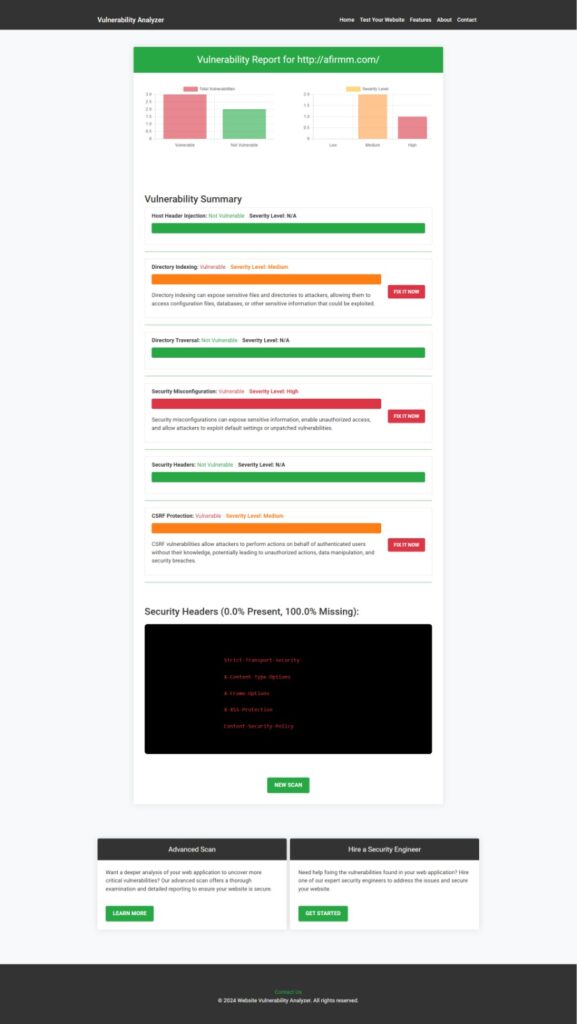
Use tools like ours to test website security free to identify risks. Below is a screenshot of our tool interface:
Detecting IDOR with Free Tools
Did you know you can detect vulnerabilities like IDOR using our free Website Security Scanner Tool? The following is an example report generated from the tool:
Learn More About Securing Your ERP Systems
If you’re managing an OpenCart system, we recommend exploring our guide:
Fix Broken Authentication in OpenCart.
For more insights into securing web applications, check out our recent post on: Best 7 Tips to Fix Broken Authentication in TypeScript ERP, Cross-Site Request Forgery (CSRF) in TypeScript.
Also, browse other blog posts at our blog for the latest cybersecurity practices.
Conclusion
IDOR vulnerabilities can have devastating consequences, especially in ERP systems that handle critical business operations. By following best practices, implementing secure coding strategies, and leveraging tools like our free Website Security Checker, you can significantly reduce these risks.
Secure your systems today and protect your business from unforeseen threats. Share your thoughts in the comments below!

Pingback: Best 10 Ways to Prevent Sensitive Data Exposure in OpenCart
Pingback: Best 7 Tips to Fix Broken Authentication in TypeScript ERP
Pingback: Prevent Sensitive Data Exposure in TypeScript: 5 Best Practices