Best 7 Tips to Prevent Server-Side Request Forgery SSRF in TypeScript ERP
Server-Side Request Forgery (SSRF) is a critical vulnerability that affects modern web applications, especially Enterprise Resource Planning (ERP) systems. It allows attackers to manipulate server-side requests, accessing internal systems and sensitive data. In this blog, we’ll explore SSRF in TypeScript-based ERP applications, with practical coding examples and actionable tips to secure your applications.

We’ll also demonstrate how you can use our tools to test website security free to assess vulnerabilities like SSRF in your applications.
What is Server-Side Request Forgery (SSRF)?
SSRF occurs when a server makes unauthorized or unsafe HTTP requests based on user input. This can lead to:
- Exposure of internal services.
- Unauthorized access to sensitive data.
- Potential Remote Code Execution (RCE) under certain conditions.
For a deeper understanding of how RCE vulnerabilities work, check out our guide on Preventing Remote Code Execution (RCE) in TypeScript.
Why SSRF is a Major Concern in ERP Systems
ERP systems handle sensitive organizational data, making them lucrative targets for attackers. SSRF vulnerabilities in ERP systems can:
- Compromise internal APIs.
- Access sensitive files on the server.
- Exploit services running behind firewalls.
To secure ERP systems, sanitizing and validating all user inputs is essential.
SSRF Example in a TypeScript ERP Application
Let’s consider a simplified TypeScript-based ERP system feature that fetches data from a user-provided URL.
Vulnerable Code Example
import axios from "axios";
import express from "express";
const app = express();
app.use(express.json());
app.post("/fetch-data", async (req, res) => {
const { url } = req.body;
try {
const response = await axios.get(url);
res.json(response.data);
} catch (error) {
res.status(500).send("Error fetching data.");
}
});
app.listen(3000, () => console.log("Server running on port 3000"));In the above code, the url parameter is directly used to make a request without validation. An attacker could exploit this to access internal services, such as:
POST /fetch-data HTTP/1.1
Content-Type: application/json
{
"url": "http://localhost:3000/admin"
}How to Prevent SSRF in TypeScript ERP Systems
1. Input Validation
Always validate user inputs to ensure they conform to a whitelist of safe URLs.
const ALLOWED_DOMAINS = ["trusted-domain.com"];
function isValidUrl(url: string): boolean {
try {
const parsedUrl = new URL(url);
return ALLOWED_DOMAINS.includes(parsedUrl.hostname);
} catch {
return false;
}
}2. Use Libraries to Restrict Requests
Use libraries like axios-restricted to restrict request origins.
3. Block Requests to Private IPs
Ensure the server does not connect to private IP ranges.
Secure Code Example
import axios from "axios";
import express from "express";
import { isValidUrl } from "./urlValidator"; // Assuming you created the validator
const app = express();
app.use(express.json());
app.post("/fetch-data", async (req, res) => {
const { url } = req.body;
if (!isValidUrl(url)) {
return res.status(400).send("Invalid URL.");
}
try {
const response = await axios.get(url);
res.json(response.data);
} catch (error) {
res.status(500).send("Error fetching data.");
}
});
app.listen(3000, () => console.log("Server running on port 3000"));Leverage Our Free Tools for SSRF Testing
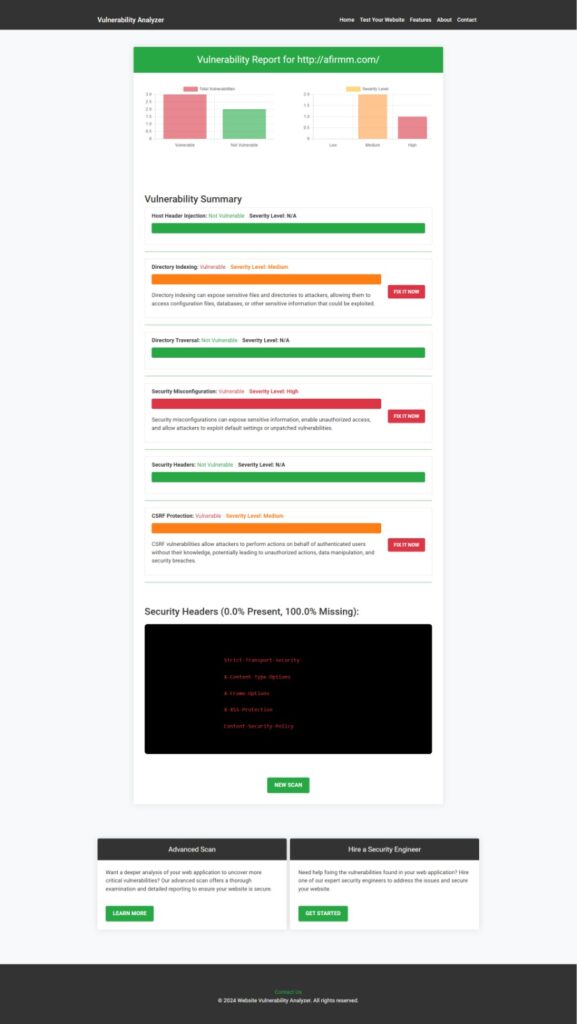
Check out our Website Security Checker to identify SSRF vulnerabilities and other security issues in your ERP applications. Below is an example screenshot of our tool in action:

Our tools also provide detailed vulnerability assessment reports. Here’s a snapshot of an SSRF vulnerability report:
Linking to Related Topics
Explore our comprehensive guide on XML Injection in OpenCart to understand similar vulnerabilities.
For a deeper dive into other vulnerabilities, check out our posts on:
- Cross-Site Scripting (XSS) in TypeScript ERP
- Preventing Remote Code Execution (RCE) in TypeScript
- Best 5 Ways to Prevent XXE in TypeScript-Based ERP Systems
- More Cybersecurity Blogs
Conclusion
Securing TypeScript-based ERP systems from SSRF vulnerabilities requires careful validation, configuration, and testing. By following the best practices and leveraging tools like our free Website Security Scanner, you can ensure your applications remain secure and resilient against attacks.
For expert cybersecurity services, contact us at Cyber Rely. Protect your systems today!
Pingback: Best 5 Ways to Prevent XXE in TypeScript-Based ERP Systems