Best Practices to Prevent Path Manipulation in TypeScript-Based ERP Systems
Path manipulation vulnerabilities in TypeScript can expose sensitive data, disrupt operations, and compromise your ERP systems. In this post, we’ll explore path manipulation, its risks, and how to mitigate these vulnerabilities with best practices and code examples.
What Is Path Manipulation?
Path manipulation occurs when attackers exploit improperly validated file paths, allowing unauthorized access to restricted directories or files. This is a common vulnerability in file-handling functions, especially in web applications using TypeScript-based ERP systems.
Real-World Example of Path Manipulation in ERP Systems
Consider a TypeScript-based ERP system that processes invoices. A user uploads a file, and the backend saves it to a specific directory. If the file path isn’t validated, an attacker can manipulate the path to access restricted files.
Here’s an example of unsafe code:
import * as fs from 'fs';
import * as path from 'path';
const uploadFile = (filePath: string) => {
const fullPath = path.join('/uploads', filePath);
fs.readFile(fullPath, (err, data) => {
if (err) throw err;
console.log(data.toString());
});
};
uploadFile('../../etc/passwd'); // Malicious input How Attackers Exploit This Vulnerability
By injecting ../ sequences, attackers can traverse directories and access sensitive system files, such as etc/passwd or application configuration files.
7 Best Ways to Prevent Path Manipulation in TypeScript
1. Validate User Input
Use strict validation to sanitize and validate user inputs. Reject file paths containing special characters like ../.
const isValidPath = (input: string): boolean => {
return /^[a-zA-Z0-9_.-]+$/.test(input);
};
if (!isValidPath(filePath)) {
throw new Error('Invalid file path');
} 2. Use Built-In Libraries
Leverage libraries like path to normalize paths and prevent directory traversal.
const fullPath = path.join('/uploads', filePath);
const normalizedPath = path.normalize(fullPath);
if (!normalizedPath.startsWith('/uploads')) {
throw new Error('Path traversal detected');
} 3. Restrict File Access
Implement file access controls to ensure only specific directories are accessible.
const allowedDirectory = '/uploads';
const fullPath = path.join(allowedDirectory, filePath);
if (!fullPath.startsWith(allowedDirectory)) {
throw new Error('Unauthorized access');
} 4. Log Suspicious Activity
Monitor and log attempts to access invalid paths for security audits.
5. Use Security Tools
Utilize tools to scan and detect vulnerabilities in your system.

6. Employ Secure File Uploads
Ensure your upload functionality limits accepted file types and sizes.
7. Perform Regular Vulnerability Assessments
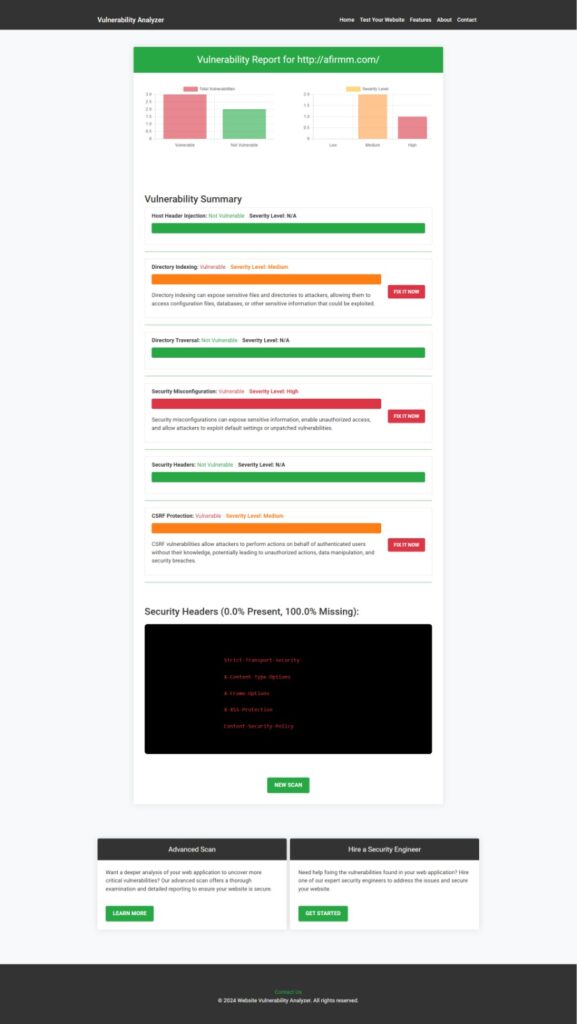
Conduct routine security assessments using tools like the free Website Security Checker. Here’s a sample vulnerability report:
Additional Insights from Our Cybersecurity Blogs
Explore our other blogs for related vulnerabilities and solutions:
- Weak Password Policies in OpenCart
- Prevent Open Redirect in TypeScript
- Fix Weak Password Policies in TypeScript
- Prevent Sensitive Data Exposure in RESTful APIs
- Unrestricted File Upload in TypeScript
For more expert tips, visit our blog page.
Why Path Manipulation Vulnerability Matter
Path manipulation can lead to:
- Data Exposure: Accessing sensitive files.
- Application Disruption: Modifying essential files.
- Unauthorized Access: Exploiting weak validations.
Implementing these measures will help safeguard your ERP system. Remember to perform regular assessments by using our free Website Security Scanner and keep your tools updated for the best protection.
Pingback: Fix Weak Password Policies in TypeScript: 7 Best Practices