Remote Code Execution (RCE) in RESTful APIs: Understanding and Securing Your Applications
The increasing reliance on RESTful APIs has brought significant benefits to modern applications but has also made them prime targets for sophisticated attacks like Remote Code Execution RCE in RESTful APIs. RCE is a critical vulnerability that allows attackers to execute malicious code on a server or endpoint, leading to unauthorized access, data breaches, and potentially full system compromise.
In this blog, we’ll dive into how RCE vulnerabilities occur in RESTful APIs, explore real-world scenarios with detailed coding examples, and provide actionable solutions to prevent them.

What is Remote Code Execution (RCE)?
Remote Code Execution is a type of vulnerability that occurs when user inputs are not adequately validated or sanitized. It enables attackers to inject and execute arbitrary code on the server, potentially leading to severe security breaches.
For example, in RESTful APIs, this often occurs when input data is directly executed as part of server-side logic, especially in cases where deserialization or command execution is involved.
Example of a Remote Code Execution RCE in RESTful API
Consider the following vulnerable RESTful API endpoint written in Node.js:
const express = require('express');
const app = express();
const exec = require('child_process').exec;
app.use(express.json());
app.post('/execute', (req, res) => {
const command = req.body.command; // User input
exec(command, (error, stdout, stderr) => {
if (error) {
console.error(`Error: ${error.message}`);
return res.status(500).send('Command execution failed');
}
res.send(`Output: ${stdout}`);
});
});
app.listen(3000, () => console.log('API running on port 3000'));
In this example, the exec() function directly executes the user-provided command, making the application vulnerable to RCE. An attacker could send a request like this:
POST /execute
{
"command": "rm -rf /"
}
The malicious command could delete critical server files or execute other harmful operations.
Securing RESTful APIs Against RCE
To prevent RCE vulnerabilities, consider the following strategies:
- Input Validation and Sanitization
Validate all user inputs to ensure they conform to expected formats. Use libraries likevalidator.jsor custom regex patterns to sanitize inputs.const validateInput = (input) => /^[a-zA-Z0-9_]+$/.test(input);app.post('/execute', (req, res) => {const command = req.body.command;if (!validateInput(command)) { return res.status(400).send('Invalid input');}// Proceed with sanitized input});
- Avoid Dangerous Functions
Avoid using functions likeexec()oreval(). Instead, implement specific functionalities without executing user-provided code. - Use Parameterized Queries
If your API interacts with a database, use parameterized queries to prevent injection attacks. - Secure Frameworks and Libraries
Regularly update and use secure versions of libraries and frameworks to prevent vulnerabilities.
Related Resources
📷 Our Free Website Security Checker Tool
Here is a screenshot of our free Website Security scanner tool identifying vulnerabilities, including RCE.

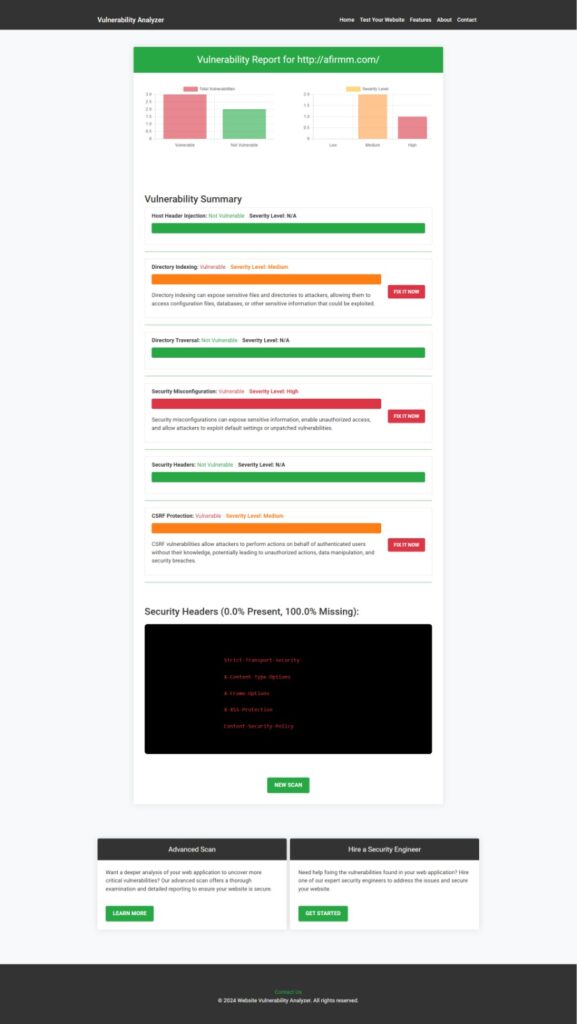
📷 Website Vulnerability Assessment Report
Below is a sample screenshot of a vulnerability assessment report generated using our tool.
Explore More About RCE in Laravel
If you’re interested in learning about RCE in the Laravel framework, check out our detailed guide on Remote Code Execution in Laravel.
Preventing Other Vulnerabilities
To strengthen your API security further, read our previous blog post on Preventing Broken Access Control in RESTful APIs.
Additionally, browse through our collection of informative posts on our blog page for more insights into cybersecurity like Preventing SQL Injection SQLi in TypeScript-Based ERP Systems.
Final Thoughts
RCE in RESTful APIs is a serious vulnerability that requires immediate attention. By implementing proper input validation, avoiding insecure functions, and regularly auditing your API’s security, you can significantly reduce the risk of exploitation.
Start securing your APIs today by utilizing our tools to test website security free and conducting comprehensive vulnerability assessments.
Pingback: SQL Injection SQLi in TypeScript-Based ERP: 3 Best Practices