Securing the Digital Gateway: A Case Study on RESTful API Penetration Testing.
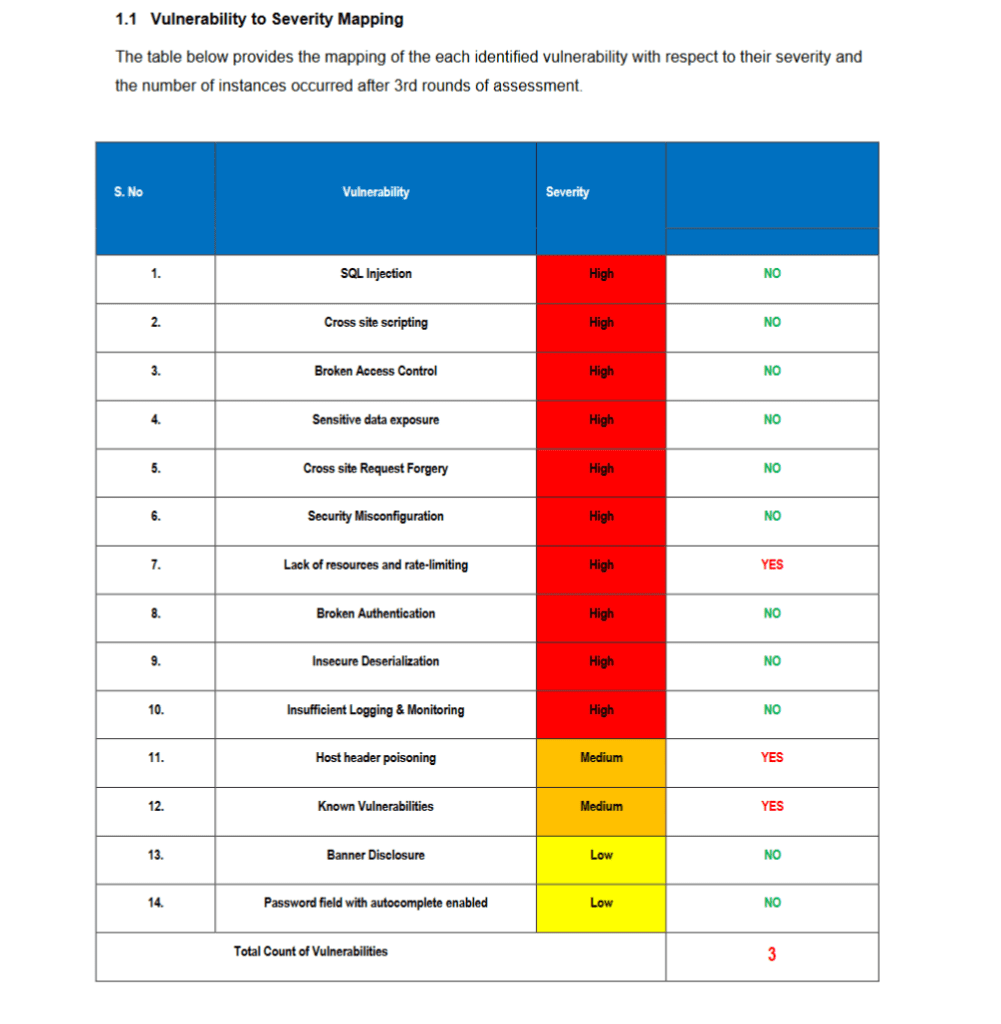
Introduction: As organizations increasingly rely on RESTful APIs as a cornerstone of their digital infrastructure, ensuring the security of these interfaces is paramount. This case study delves into Cyber Rely’s comprehensive penetration testing engagement, uncovering critical vulnerabilities including Lack of Resources and Rate-Limiting, Host Header Poisoning, and Known Vulnerabilities, and providing actionable insights to fortify the client’s API security posture.
Client Profile: Our client, a leading fintech company, operates a suite of RESTful APIs that serve as the backbone of their digital platform, facilitating seamless interactions between clients and financial services. Recognizing the inherent security risks associated with API exposures, they enlisted Cyber Rely’s expertise to conduct a thorough penetration testing assessment.
Objectives:
- Identify and mitigate vulnerabilities within the client’s RESTful APIs, focusing on Lack of Resources and Rate-Limiting, Host Header Poisoning, and Known Vulnerabilities.
- Assess the effectiveness of existing security controls and defensive measures implemented within the API infrastructure.
- Simulate real-world cyber attacks targeting the APIs to evaluate resilience and response capabilities.
- Provide actionable insights and recommendations to bolster the security of the RESTful APIs and mitigate identified risks.
Methodology: Cyber Rely’s team of penetration testers employed a systematic approach to assess the security posture of the client’s RESTful APIs, encompassing the following phases:
- Reconnaissance and Information Gathering: Cyber Rely conducted thorough reconnaissance to gain insights into the API architecture, endpoints, and potential attack vectors.
- Vulnerability Identification: Leveraging a combination of automated scanning tools and manual techniques, Cyber Rely identified vulnerabilities related to Lack of Resources and Rate-Limiting, Host Header Poisoning, and Known Vulnerabilities.
- Exploitation and Testing: Through ethical hacking methodologies, Cyber Rely’s penetration testers attempted to exploit identified vulnerabilities, simulating real-world cyber attacks to assess the APIs’ resilience.
- Reporting and Remediation: Cyber Rely compiled a detailed report outlining the findings, including actionable recommendations for remediation and enhancement of the API security posture.
Key Findings:
- Lack of Resources and Rate-Limiting: Vulnerabilities were identified that allowed attackers to exhaust API resources and bypass rate-limiting controls, leading to denial of service (DoS) attacks and potential service disruptions.
- Host Header Poisoning: The penetration testing revealed weaknesses in input validation mechanisms, enabling attackers to manipulate host headers and redirect API requests to malicious servers, leading to data exfiltration or unauthorized access.
- Known Vulnerabilities: Cyber Rely identified instances where the client’s RESTful APIs were vulnerable to known security flaws, such as outdated software versions, insecure authentication mechanisms, and inadequate encryption protocols, posing significant risks to data confidentiality and integrity.
Recommendations and Implementation: Armed with the findings from the penetration testing engagement, Cyber Rely collaborated closely with the client to implement targeted remediation measures. Recommendations included:
- Implementing Resource Limits and Rate-Limiting: Configuring API endpoints to enforce resource limits and rate-limiting controls to mitigate the risk of DoS attacks and resource exhaustion.
- Enhancing Input Validation: Implementing strict input validation mechanisms to prevent host header manipulation and other injection attacks, ensuring the integrity and authenticity of API requests.
- Patching Known Vulnerabilities: Updating API dependencies, software versions, and security protocols to address known vulnerabilities and mitigate the risk of exploitation by malicious actors.
Results and Impact: Through proactive collaboration with Cyber Rely, our client achieved significant improvements in the security posture of their RESTful APIs. Key outcomes included:
- Mitigation of Critical Vulnerabilities: Prompt remediation actions were undertaken to address identified vulnerabilities, reducing the risk of DoS attacks, data manipulation, and known security exploits.
- Strengthened API Security Controls: The implementation of recommended security measures, including resource limits, input validation, and vulnerability patching, bolstered the resilience of the client’s APIs against cyber threats.
- Enhanced User Trust: By prioritizing API security and safeguarding sensitive data, our client demonstrated their commitment to protecting client assets and preserving trust and confidence among stakeholders.
Conclusion: In an era marked by escalating cyber threats, securing RESTful APIs is paramount to safeguarding digital assets and maintaining operational integrity. Through strategic collaboration with Cyber Rely, our client successfully addressed critical vulnerabilities in their API infrastructure, exemplifying the transformative impact of penetration testing and proactive security measures in fortifying digital gateways against evolving cyber threats.
Check out our related blog post on How to Prevent SQL Injection SQLi in RESTful APIs in 2024. You can also take a look at our other post on React JS Vulnerability Assessments and Penetration Testing Case Study for more information about cyber security.