Client Overview: Cyber Rely, a prominent cybersecurity firm, was commissioned to conduct a comprehensive vulnerability assessment of CloudBank, a Java-based web application designed for online banking services. The client, CloudBank (demo)., sought to identify and rectify potential security flaws to ensure the confidentiality, integrity, and availability of their users’ financial information.
Project Scope: Cyber Rely was tasked with assessing the security posture of the CloudBank web application, focusing on identifying vulnerabilities such as Cross-Site Scripting (XSS), Session Fixation, Cross-Site Request Forgery (CSRF), Malicious File Upload, Broken Authentication, Known Vulnerabilities, Missing Headers Security, Banner Disclosure, and Password Field with Autocomplete Enabled.
Methodology: Cyber Rely adopted a systematic approach to evaluate the security of the CloudBank application. The methodology included:
- Reconnaissance: Understanding the architecture, technologies used, and the overall functionality of the web application.
- Vulnerability Identification: Utilizing automated tools and manual testing techniques to identify potential security vulnerabilities.
- Exploitation: Verifying the existence and severity of vulnerabilities through controlled exploitation.
- Documentation: Thorough documentation of identified vulnerabilities, including their impact and recommended remediation measures.
- Reporting: Providing a detailed report to the client, highlighting the findings and prioritizing remediation actions based on the severity of the vulnerabilities.
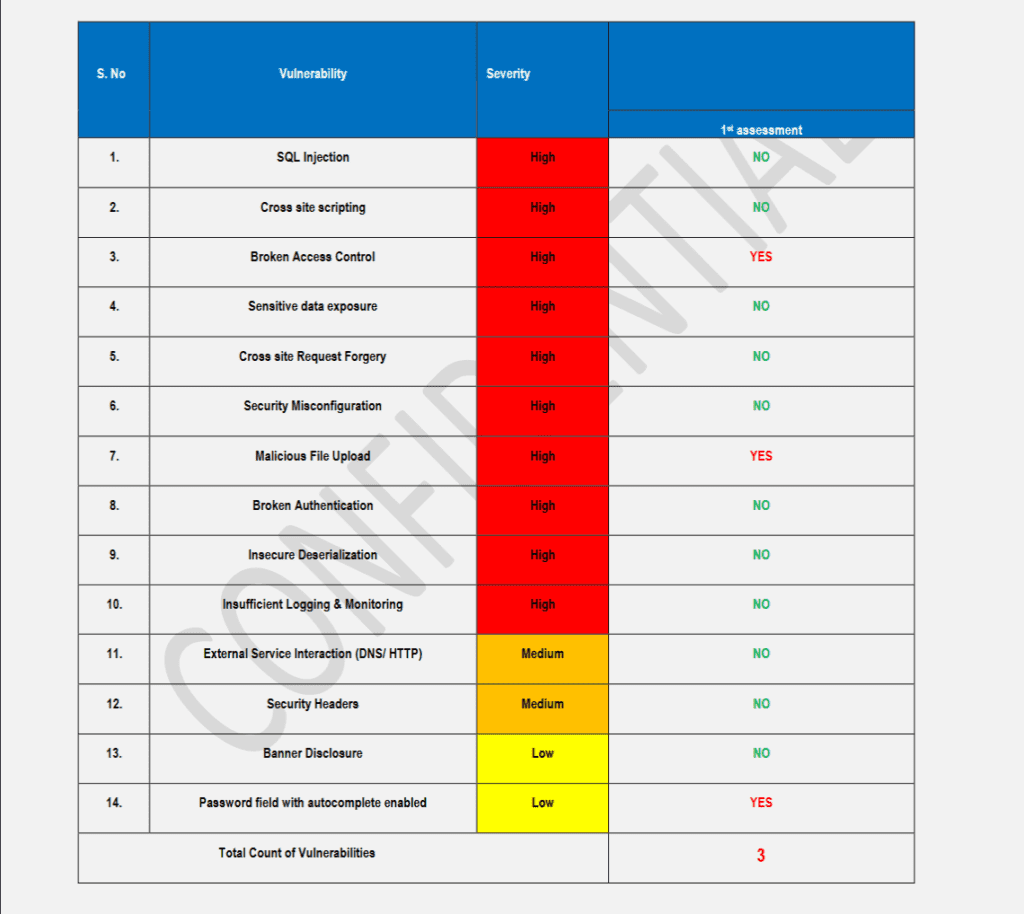
Key Findings of Vulnerability Assessment of CloudBank:
- Cross-Site Scripting (XSS): Multiple instances of reflected and stored XSS vulnerabilities were discovered, allowing attackers to execute arbitrary JavaScript code within the context of the web application.
- Session Fixation: The web application lacked proper session management mechanisms, making it susceptible to session fixation attacks where an attacker can hijack a user’s session.
- Cross-Site Request Forgery (CSRF): CloudBank was found to be vulnerable to CSRF attacks, enabling attackers to execute unauthorized actions on behalf of authenticated users.
- Malicious File Upload: The application did not adequately validate file uploads, facilitating the potential for malicious files to be uploaded and executed on the server.
- Broken Authentication: Weak authentication mechanisms and improper session handling exposed sensitive user authentication data, increasing the risk of unauthorized access.
- Known Vulnerabilities: The application utilized outdated libraries and frameworks with known security vulnerabilities, exposing it to exploitation by attackers.
- Missing Headers Security: Critical security headers, such as Content Security Policy (CSP) and X-Frame-Options, were missing, leaving the application vulnerable to various attacks.
- Banner Disclosure: Detailed server information and version numbers were disclosed in response headers, aiding attackers in crafting targeted attacks.
- Password Field with Autocomplete Enabled: Enabling autocomplete in password fields could lead to credential exposure and compromise user accounts.
Recommendations:
- Implement input validation and output encoding to mitigate XSS vulnerabilities.
- Adopt secure session management practices to prevent session fixation attacks.
- Utilize CSRF tokens and implement strict referer checks to mitigate CSRF vulnerabilities.
- Implement file upload validation to restrict the types and sizes of uploaded files.
- Strengthen authentication mechanisms, such as multi-factor authentication and password hashing, to mitigate broken authentication risks.
- Regularly update and patch dependencies to address known vulnerabilities.
- Configure security headers, such as CSP and X-Frame-Options, to enhance the application’s security posture.
- Minimize server information disclosure by configuring server banners appropriately.
- Disable autocomplete for password fields to prevent credential exposure.
Conclusion: The vulnerability assessment conducted by Cyber Rely revealed several critical security weaknesses in the CloudBank web application. By addressing the identified vulnerabilities and implementing the recommended remediation measures, CloudBank Inc. can significantly enhance the security of their online banking platform, safeguarding the confidentiality and integrity of their users’ financial data. Regular security assessments and proactive risk management are essential to mitigate emerging threats and ensure continued resilience against evolving cybersecurity challenges.
Comprehensive Penetration Testing Services
While vulnerability assessments like those we offer for Cloudbank are critical for identifying potential weaknesses, penetration testing goes a step further by simulating real-world attacks to test the effectiveness of your security measures. If you’re looking for more in-depth testing services, including network, application, or cloud penetration testing, our team at Pentest Testing provides thorough assessments tailored to your specific needs. Visit our site to learn how our advanced techniques can help fortify your systems against emerging threats.