Best 5 Ways to Prevent XXE in TypeScript-Based ERP Systems
XML External Entity (XXE) Injection is one of the most dangerous vulnerabilities plaguing modern web applications, including ERP systems. This vulnerability allows attackers to exploit XML parsers by embedding external entities into the XML code. Once processed, these entities can access sensitive data, execute remote code, or even launch Denial of Service (DoS) attacks.

For developers using TypeScript-based ERP systems, ensuring the security of XML parsers is critical. This post will guide you through actionable strategies to prevent XXE in TypeScript-based ERP applications. With practical examples, insights, and a focus on using modern tools, you’ll have a comprehensive approach to safeguarding your systems.
We’ll also introduce you to our free Website Security Checker tool, a resource that can identify XXE vulnerabilities in your applications. Take a look at the screenshot below to explore the tool:

What is XXE in TypeScript-Based ERP Systems?
An XML External Entity (XXE) vulnerability occurs when XML parsers process external entities embedded in the XML code. In TypeScript-based ERP systems, where XML is often used for data exchange, a single flaw in XML parsing configuration can expose the application to XXE attacks.
Why Focus on XXE in TypeScript-Based ERP Systems?
ERP systems manage sensitive business processes, such as inventory, payroll, and client data. A breach caused by XXE could compromise critical information, disrupt operations, and lead to financial and reputational damage.
Here’s an example of a simple XML document that can be exploited using XXE:
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "file:///etc/passwd">]>
<foo>&xxe;</foo>In this case, if the parser processes the external entity (xxe), the attacker gains access to the server’s password file.
Common XXE Attack Scenarios
- File Disclosure:
Attackers use XXE to access sensitive files, such as API keys, configuration files, or user data. - Server-Side Request Forgery (SSRF):
External entities can be manipulated to send unauthorized requests to internal systems. - Denial of Service (DoS):
Recursive entity expansion can overwhelm server resources, causing application downtime.
Best Practices to Prevent XXE in TypeScript-Based ERP Systems
1. Disable External Entity Processing (XXE in TypeScript)
The most effective way to prevent XXE in TypeScript-based ERP systems is to disable external entity processing in your XML parser.
Example in TypeScript:
import * as xml2js from 'xml2js';
const parser = new xml2js.Parser({
explicitEntityParsing: false, // Disables external entities
});
const xmlData = `<note><to>User</to></note>`;
parser.parseString(xmlData, (err, result) => {
if (err) {
console.error("Error parsing XML", err);
} else {
console.log(result);
}
});Why This Works:
By disabling external entities, the parser ignores potentially malicious content, significantly reducing the risk of XXE attacks.
2. Use a Secure XML Parsing Library (XXE in TypeScript)
Switching to modern libraries like fast-xml-parser can prevent XXE vulnerabilities out of the box.
Example Using fast-xml-parser:
import { XMLParser } from 'fast-xml-parser';
const parser = new XMLParser({
ignoreExternalEntities: true, // Automatically prevents XXE
});
const xmlData = `<note><to>User</to></note>`;
const result = parser.parse(xmlData);
console.log(result);Advantages of Secure Libraries:
- Built-in safeguards against XXE
- Faster parsing with minimal overhead
3. Validate XML Input Against a Whitelist
Allow only specific XML elements and attributes by validating input against a whitelist. This approach ensures that unexpected data is rejected before processing.
import * as validator from 'fast-xml-parser';
const xmlData = `<note><to>User</to></note>`;
const isValid = validator.validate(xmlData);
if (!isValid) {
throw new Error("Invalid XML input detected.");
}Why Input Validation is Essential:
Attackers often exploit overly permissive parsers. By validating XML input, you add a robust layer of security to your TypeScript-based ERP system.
4. Monitor for Vulnerabilities Using Automated Tools
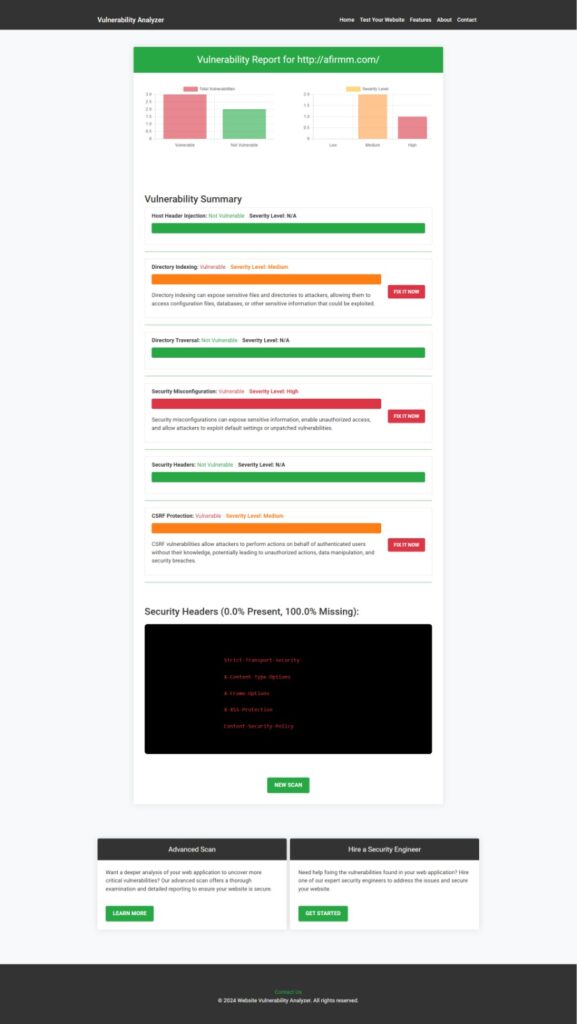
Regular scanning with automated tools is critical to identifying and addressing potential XXE vulnerabilities. Our free Website Security Scanner tool is designed to scan for security gaps, including XXE.
Below is a sample vulnerability assessment report generated by our tool:
5. Secure Error Handling and Logging
Attackers can exploit verbose error messages to learn about your system. Implement strict error handling and logging mechanisms to ensure no sensitive information is exposed.
Additional Resources on TypeScript Security
To further enhance the security of your TypeScript-based ERP systems, explore our related guides:
- How to Prevent SSRF in TypeScript
- Prevent Directory Traversal in TypeScript ERP
- Prevent Sensitive Data Exposure in TypeScript
- Browse our cybersecurity blog for more insights.
For OpenCart users, check out our guide on fixing directory traversal vulnerabilities.
Conclusion
Addressing XXE vulnerabilities in TypeScript-based ERP systems is crucial for maintaining secure operations and protecting sensitive data. By implementing the strategies outlined here, such as disabling external entity processing, using secure libraries, and leveraging automated tools like ours to test website security free, you can significantly enhance your system’s security.
For professional assistance in vulnerability assessment and penetration testing, reach out to Pentest Testing Corp. Together, we can create safer digital environments.

Pingback: Prevent Directory Traversal in TypeScript ERP: Best 7 Ways